Data Protection: Now More Important than Ever
Data protection is increasingly more important for businesses as cyber attacks become more frequent and more destructive. The number of attacks has increased as hackers have taken advantage of the work-from-home model adopted during the pandemic. According to Fintech News, 80% of businesses have seen an increase in attacks this year. Without reservation, hackers look for vulnerabilities between home and office networks to steal sensitive data. As we’ve discussed previously, remote work isn’t likely to be going anywhere soon, so it’s vital that you boost the security of your systems to defend against potential damage. And let’s be honest: if you are still using customized Excel spreadsheets and off-the-shelf accounting packages, your system is most likely at risk.
One way to combat these threats is to move to cloud-based applications and storage. Depending on the foundational hosting platform, the cloud can offer increased protection from malicious forces. Business applications like CRESSblue provide additional security features to help secure your data by partnering with a strong, leading-edge hosting platform.
While adoption of this trend continues to rise, it can still be nerve-wracking to make the leap. We know you probably have a lot of questions: What kind of protection does the cloud offer? Does the hosting service have access to my data? Can the cloud really protect from attacks?
Let’s take a look at how CRESSblue and its built-in security features compare with a traditional in-house set-up.
Enterprise-level data protection at a fraction of the cost
Without a doubt, information sharing through Excel and email increases the risk of security leaks. With a cloud-based solution, the hosting platform features built-in data protection. CRESSblue uses Microsoft Azure’s cloud-computing platform to host our software. Microsoft is a trusted name and one of the top three major cloud-based hosting services in the technology industry. We selected Azure as a preferred service for our products due to their commitment to cyber security and robust protection features. Achieving such high-level security in-house would require a huge investment of both time and money. And even then, the strength of the data protection would only be as good as the weakest link in your system. While no security system is bulletproof, you will enjoy the benefits that come from partnering with an industry-leading giant in the technology field.
Control access to sensitive data with defined access and permissions
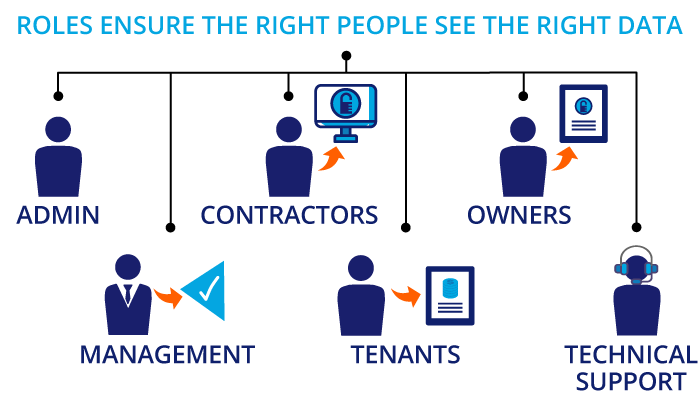
Manage your risk by ensuring that only authorized personnel have access to sensitive data. It’s easy to do with CRESSblue. How? Permissions control who has access and maintain a hierarchy of role-based security clearance. In fact, users may have varying levels of access depending on their level of responsibility. Every process is role-based and requires separate permissions for data entry and approvals. You can also set up separate permissions for viewing and editing.
Give careful thought to the designation of user roles. Review each employee’s role and the type of information they need to access daily. Think about the levels of access they require.
For example, different types of roles may include:
- Administrative for general use
- Management for approval processes
- Tenant users for administration or accounting
- Owners with access to property-specific reports
- Technical support users
You can determine exactly how much data each user can view and edit by defining these roles. By implementing role-based access control, your company can save time and reduce red tape. This is especially true when new hires come on board or when an employee changes their role. You can easily revoke access when an employee leaves the company or buildings change ownership. In like manner, you can assign pre-determined roles and access through external portals to third-party users. This avoids the need to set them up on internal systems. Administrators can also provide multiple role permissions for users who may need specific data for a time-based project. And, later remove them once the project is complete.
Additional layers of data protection provide stronger security
Passwords alone will not keep hackers out. For that reason, multi-factor authentication is another feature that can provide added security. This requires the user to perform a second step of verification to complete the login process. This step may include answering a security question. Or, it may involve entering a personal identification number, biometric or token. CRESSblue also uses a second device and authentication app. In short, this reduces the risk of a single device being hacked or stolen to gain access to sensitive data systems. Once the user has been authorized, CRESSblue uses short-lifespan security tokens to confirm the identity of users. This is similar to the way a bank uses tokens to secure your session for online banking. It contains information about the user and the level of access permitted. Unauthorized users are denied access without a token.
You can configure the system in a variety of ways. It can remember the user device, so it does not require validation each time. It can have the authentication expire after a period of time or it can require two-factor identification every time the user logs on. Password strength is enforceable on several levels and a single password sign-on is disabled. You can also configure password change schedules, as well as trigger system lockouts after several failed sign-in attempts.
We’ve got your back(up)
Automatic and frequent cloud backups mean there is no need to schedule regular in-house system backups of your CRESSblue data. This means your IT department can focus on other tasks. Moreover, there’s no need to house physical storage units, saving your business time and money.
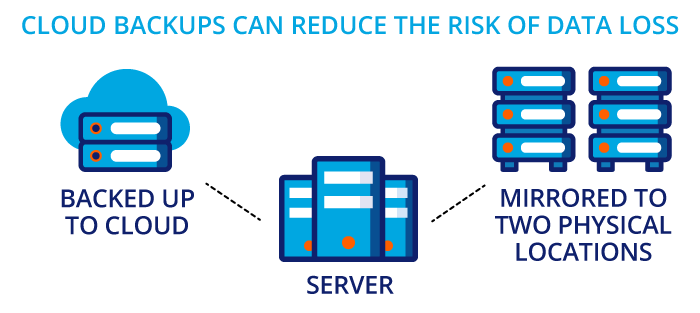
In the event of a data emergency, your systems can be easily and quickly restored. Your data is stored on the cloud and is mirrored to at least two physical locations. On the other hand, recovering files from a local office server may not be so simple. This is especially true if the storage units are physically damaged. In addition, data from individual devices may not be captured in the recovery. And this is assuming that you have a dedicated IT department. At smaller firms, staff may be backing up to easy-to-lose external hard drives. Or, worse, staff may not be making daily backups at all.
Privacy is not an issue
Your tenants trust you to keep their personal data safe. But are you confident that you can keep their information safe with your current systems? Similarly, proprietary corporate data is the lifeblood of the organization. Any breach of this data can be harmful to the business. With the data protection offered by CRESSblue, only those who have authorization can access your files. Your company holds all rights and interest in the data stored online. Equally important, the hosting service does not access your data in any way. Embedded privacy controls ensure that no unauthorized users can view your data. Multi-level authentication and access control enhance data protection.
Data protection from viruses and malicious attacks
Hackers are becoming more sophisticated, but security has also become stronger. The hosting platform uses a variety of security measures that work with browser security. Plus, our network architecture features multi-layered security features that provide robust protection against any external threats. The CRESSblue database is layered behind the hosting software. This means that unauthorized users can only interact with the front-end web browser portion; they do not directly access the database.
Any data put into the CRESSblue software entry fields is validated before it is written to the database. This helps prevent any unusual or malicious uploads from infiltrating the database. Furthermore, the hosting platform also includes real-time intrusion detection monitoring. The support centre is instantly alerted to any suspicious activity on our client accounts. If any threats are detected, automated steps are taken to react to the situation immediately.
Centralized data
Remote work is the new norm, and thus it is more important than ever to ensure all employees can access your systems anytime, anywhere. Truly, cloud-based solutions can make it easier for staff to work remotely because they are much easier to implement than on-site systems. Sure, remote workers can access in-house documents by VPN software. However, it often slows down the computer or experiences frequent connection breaks. Besides, not all VPN programs are compatible with different types of computer systems. You can easily use any device, including tablets and smartphones, to access cloud-based software.
Centralization keeps one set of data updated with the latest information. Consequently, this avoids duplication of work and increasing efficiency. Have you ever had an employee go off sick or leave the company, and no one could access their files because they didn’t know their computer password? With cloud-hosted files, that’s no longer an issue. Anyone with administrative permissions can access user files and assign them to a different staff member.
Data distribution
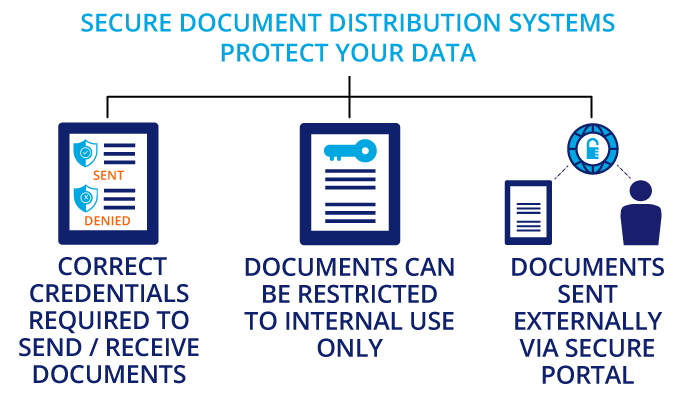
Unfortunately, security features can’t prevent staff from deliberately sharing information with external contacts. Similarly, it can’t stop them from using insecure methods of data transfer in their workflows. What does this look like in practice? It can be as simple as saving a file to their device and emailing it to a legitimate contact. In that simple process, multiple avenues of risk exposure may be created. Did they use a secure network or was it a public-access open network like an airport lounge? Was their device secure or was it a personal device without any protection, like their phone or family-use tablet? Also, email is not a secure or encrypted method for transferring personal or confidential data. Did the right recipient get the data, or was it accidentally sent to the wrong person? So many things could go wrong in that very common workflow!
CRESSblue uses document distribution systems to secure portals. This does several security tasks for you. One, document distribution rules can prevent documents from being sent by someone without the correct authorization, and to someone without the correct credentials. Two, documents can be restricted to internal use only. Three, if the documents are permitted to be shared externally, they are sent to a secure portal and the user gets a notification to access it, just like getting a notice your bank statement is available for viewing at your bank website. The entire workflow and document distribution process is secured within the system.
It’s important to do your part too
All the world’s security features won’t keep you safe in the cloud if you haven’t identified vulnerabilities on your own network. That’s why it’s crucial to ensure that you use preventative measures to safeguard your data. Think your business is too small to be targeted? Think again. Nearly half of all data breaches target small to medium-sized businesses.
It’s also important to note that not all threats are from external malicious forces. IBM’s recent “Cost of Data Breach Report 2020” showed that while 42% of Canadian data breaches were caused by malicious attacks and 35% were due to system glitches, 23% were also attributed to human error. Sharing confidential information with the wrong person, clicking on a phishing link, not updating internal security programs and incorrect authorizations can all expose the system to a data breach. That’s why it’s essential to make sure employees follow proper computer protocols to prevent breaches from happening in the first place.
There are several ways that you can reinforce data protection from the local level:
- Have employees update passwords to company systems regularly. According to the 2019 Verizon Data Breach Report, 80% of all cyber attacks involve a weak or stolen password. Changing passwords frequently reduces the chance that hackers can steal these credentials. Enforcing unique passwords with multiple character requirements will also help keep them secure. The best passwords are at least 10 characters long and include upper- and lower-case letters, symbols and numbers.
- Install anti-malware software on all of your computers or your network. All it takes is one employee to accidentally click on a very real-looking email that contains a virus to bring the whole system down. Anti-malware software identifies threats and removes them before they have a chance to infect your computers.
- Keep your software updated to ensure you have the latest version of the programs you use regularly. Updates often include security fixes as well, thus eliminating potential wormholes for attackers to enter. Don’t forget to install patches when required to eliminate bugs that may make weaken the system.
- Make sure all devices are updated too. Any device used to access your systems – from desktops and laptops to smartphones and tablets – needs to be patched and updated regularly. An insecure device has the potential to expose a hole in your security.
- Secure your Wi-Fi systems. And that doesn’t mean just adding password protection. It should also be both encrypted and hidden. Leaving your Wi-Fi open provides a gateway to your network and leaves the system vulnerable to cyber attacks. Activating network encryption, adding a firewall and changing the router’s default settings will all help to secure the network.
- Provide training for your employees to help them recognize security threats. Likewise, make them aware of best practices to keep your clients’ data safe. Training should include how to identify phishing scams, ransomware, spam and malware. Further, it should cover avoiding the use of open public-access Wi-Fi networks, as well as the importance of password security. Consider integrating cyber security training into your onboarding processes and running a refresher every couple of years.
- Create a computer use policy covering rules and guidelines for password protection, Internet access, data transfer, email precautions and compliance or legal concerns. Outline clear expectations and provide details as to what constitutes appropriate use and what does not. Employees are on the frontline of defence. Further, make sure you engage them in the policy’s development so they feel like they are part of the process and want to protect your assets. Instilling the right mindset from the top down will go a long way to encouraging employees to do the right thing.
Taking these precautions will help mitigate the risk of a threat to your computer systems. And moving your business processes to a cloud-based application will vastly improve your security.
Don’t take chances with your data. With CRESSblue, you can rest assured that you are upgrading your business systems to a world-class technology solution backed by enterprise-level data protection. Book a demo or schedule a call to learn more about our security features.
Disclaimer
This article was accurate as of December 2020. Technology is always advancing. CRESSblue specifications are subject to change without notice. Always check with your CRESSblue account administrator and your contract terms for the most current specifications. This article is for informational purposes only and is not intended as professional advice; please consult a competent professional for advice specific to you. This blog is written to stimulate thinking on concepts related to commercial leasing. Please join the discussion with your experiences.

Martin Sommer, CEO, CRESS Inc.
Martin is a founder and the CEO of CRESS Inc., a Canadian SaaS company that automates lease administration and asset management. Martin also manages Karanda Properties Limited industrial portfolio as Director of Operations in all areas of commercial property management, including new development, asset management, capital expenditures, operations, leasing and lease administration of the industrial portfolio. Martin writes about property management workflow and issues. Book Martin to speak at your industry event.












[…] enterprise-level hosting services such as Microsoft Azure, Amazon or IBM, which provide a much stronger protection level than can be implemented at the local […]